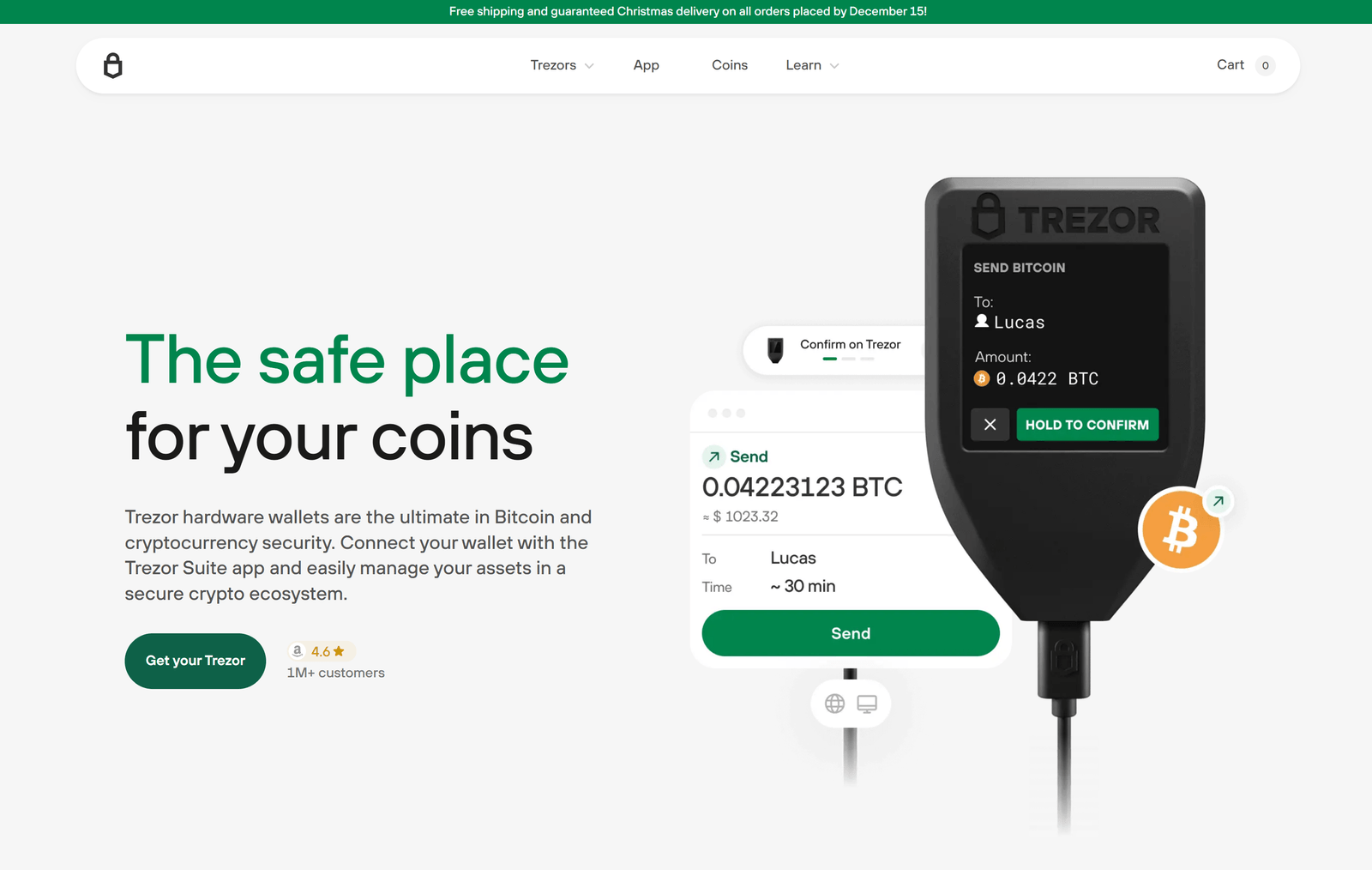
Getting Started with Trezor: Secure Crypto Storage
Introduction to Trezor and Its Importance
In the ever-evolving landscape of cryptocurrency, safeguarding digital assets is paramount. Trezor, developed by SatoshiLabs, stands as a beacon of security, offering hardware wallets that prioritize user privacy and control. Navigating to trezor.io/start marks the first step toward securing your cryptocurrencies with a device trusted by millions. This guide elucidates the setup process, security features, and best practices for using Trezor hardware wallets, ensuring your digital wealth remains protected against cyber threats.
Why Choose Trezor?
Trezor hardware wallets, including the Trezor Model One, Model T, Safe 3, and Safe 5, are engineered to provide robust security through offline key storage. Unlike software wallets, which are susceptible to hacking, Trezor devices store private keys in a secure, isolated environment, mitigating risks from malware and phishing attacks. The open-source firmware enhances transparency, allowing users to verify the integrity of the device’s operations. Additionally, Trezor’s intuitive interface, via the Trezor Suite application, caters to both novices and seasoned crypto enthusiasts.
Step-by-Step Setup Guide for Trezor
Step 1: Unboxing and Initial Inspection
Upon receiving your Trezor device, verify the packaging for authenticity. The Trezor Model T, for instance, features a security hologram over the USB-C port, ensuring the device has not been tampered with. Inside the box, you’ll find the hardware wallet, a USB cable, recovery seed cards, and a magnetic holder for convenient storage. Before proceeding, ensure the device’s firmware is genuine by checking for pre-installed software, which could indicate compromise.
Step 2: Accessing Trezor.io/start
Open a secure browser and navigate to trezor.io/start. Ensure the URL uses HTTPS to confirm a secure connection. The website automatically detects your device model (e.g., Trezor Model T or Safe 5) and guides you through the setup process. Select your device from the visual menu to proceed.
Step 3: Installing Trezor Suite
Download the Trezor Suite application, available for Windows, macOS, Linux, iOS, and Android. This software serves as the interface for managing your wallet. After installation, connect your Trezor device to your computer or mobile device via the provided USB cable. Trezor Suite will prompt you to install the latest firmware, ensuring your device is equipped with the most recent security updates.
Step 4: Creating a New Wallet
From the Trezor Suite interface, select “Create New Wallet.” You’ll be presented with two options: a Standard Single-share Backup or an Advanced Multi-share Backup (Shamir Backup). The Standard Backup generates a 12-word recovery seed for the Trezor Model T or a 20-word seed for the Trezor Safe 5, providing sufficient entropy (128 bits or more) for robust security. The Shamir Backup, exclusive to the Model T and Safe 5, allows you to split your seed into multiple shares, enhancing recovery flexibility. For example, a 3-of-5 share setup requires three shares to restore your wallet, mitigating the risk of a single point of failure.
Follow the on-screen prompts to confirm your choice on the device. The recovery seed will be displayed on the Trezor’s screen, not on your computer, to prevent exposure to potential keyloggers. Write down the seed words on the provided recovery cards and store them in a secure location, such as a safe or a bank vault. Never store your seed digitally or share it with anyone.
Step 5: Setting a PIN and Passphrase
Next, set a PIN to protect your device from unauthorized access. The Trezor Model T and Safe 5 allow PIN entry directly on the device’s touchscreen, enhancing security. For additional protection, enable the passphrase feature, which creates hidden wallets accessible only with an extra word of your choosing. This feature ensures that even if someone gains access to your recovery seed, they cannot access your funds without the passphrase.
Step 6: Finalizing Setup and Exploring Trezor Suite
After configuring your wallet, Trezor Suite will guide you to the wallet homepage. Here, you can manage multiple cryptocurrencies, including Bitcoin, Ethereum, and various altcoins. The interface supports features like transaction labeling, CSV/PDF export, and direct trading via integrated exchanges. For privacy-conscious users, Trezor Suite offers dark mode and multilingual support, including English, Spanish, and Japanese.
Advanced Security Features
Trezor’s security is bolstered by its adherence to industry standards like BIP-39 for seed phrases and SLIP-39 for Shamir Backup. The Trezor Safe 5 introduces a 20-word backup standard, offering a balance between simplicity and enhanced security through multi-share recovery. The device’s Secure Element (in Safe 3 and Safe 5) adds an extra layer of protection against physical attacks. Additionally, Trezor’s lack of Bluetooth connectivity eliminates potential wireless vulnerabilities, a feature that distinguishes it from competitors.
Best Practices for Trezor Users
- Safeguard Your Recovery Seed: Store your seed phrase in multiple secure locations, such as a fireproof safe or with trusted individuals. Consider using a metal backup solution like Billfodl for durability.
- Verify Transactions on Device: Always confirm transaction details on your Trezor’s screen to prevent man-in-the-middle attacks.
- Beware of Phishing: Only access trezor.io/start or Trezor Suite through official channels. Verify URLs and avoid clicking suspicious links.
- Regular Firmware Updates: Keep your device’s firmware updated via Trezor Suite to benefit from the latest security patches.
- Test Recovery Process: Periodically simulate wallet recovery with your seed phrase to ensure its accuracy, avoiding errors like misspelled words (e.g., “gift” vs. “giraffe”).
Troubleshooting Common Issues
If you encounter an “Invalid recovery seed” error, verify that your seed words match the BIP-39 wordlist and are entered in the correct order. For Trezor Safe 5 users, note that the 20-word seed is supported by limited software wallets (e.g., Electrum, Rabby). If your seed includes non-standard words like “academic,” contact Trezor support, as this may indicate a compatibility issue or user error.
Conclusion
Trezor hardware wallets, accessible via trezor.io/start, offer an unparalleled blend of security, usability, and flexibility. By following this guide, you can confidently set up your Trezor device, leverage advanced features like Shamir Backup and passphrases, and protect your cryptocurrency from cyber threats. As the crypto landscape grows increasingly complex, Trezor remains a steadfast guardian of your digital assets, empowering you to navigate the blockchain with peace of mind.
Made in Typedream